One of the best ways to keep your WordPress website secure is to check for potentially malicious code often on your website. Whenever you find any vulnerability, you can take immediate corrective actions before allowing anyone to exploit it and allegedly enter into your WordPress admin panel.
There is no wonder that hackers target WordPress websites hugely because it is the most popular CMS in the market. Out of the box, there are several ways to make your WordPress installation more secure. However, the harsh reality is only a fraction of sites follow them. This makes WordPress one of the easiest targets for hackers.
{autotoc}
Recommended Reading: 17 ways to prevent WordPress hacking
9 WordPress Vulnerability Issues
1. Cheap WordPress Hosting
If you opt for your WordPress hosting solely based on hosting, you're more than likely to encounter a number of WordPress vulnerabilities. This is because cheap hosting are more than likely to be incorrectly set up and not segregated from each other correctly.
This means that sites that have been exploited on one installation could spread to unrelated websites that are hosted on the same server. This issue could also happen if you host several websites for a number of your clients on the same hosting account.
In this case, once again, if anyone of your websites gets compromised, the infection could spread to ALL of the websites in your account. You need to be careful to ensure that you are using a setup such as a VPS, that allows you to create separation between the different hosted websites.
Another problem with cheap hosting is the question of "dodgy neighbours". Cheap hosting will tend to attract spammy or dodgy clients - these could mean that the actual server where the website is hosted gets blacklisted or spamlisted.
FIX: First and foremost, make sure that you don't opt for the cheapest hosting that you can find. Instead opt for hosting that makes security a priority. Secondly, if you host websites for your clients, make sure that you compartmentalize the different clients by creating different users for each client.
IMH
Do you want a fast website?
Who am I kidding? Don't we all?
So why do so many of us struggle?
The biggest challenge is usually finding a fast, reliable hosting company.
We've all been through the nightmares - support take takes forever or doesn't resolve our problem always blaming something on your side...
But the biggest bummer is that the website always feels slow.
At CollectiveRay we host with InMotion hosting and our website is stupid fast. We run on a custom stack of LightSpeed server setup on MariaDB with a PHP7.4 engine and fronted through Cloudflare.
Combined with our front-end optimizations we reliably server 6000 users every single day, with peaks of 50+ simultaneous users.
Want to get a fast setup like ours? Transfer your site for free to InMotion hosting and get our 50% OFF on current pricing.
Try InMotion Hosting with 50% OFF for CollectiveRay visitors in January 2026 ONLY!
2. Weak WordPress Logins and Passwords
The address of the WordPress login is common knowledge and hacking scripts exist whose sole purpose is to brute force common password combinations or try a list of passwords that have leaked from other sites.
This means that if you use a weak password such as admin/admin, or admin/password or other stupidly simple password combinations, you are introducing a serious WordPress vulnerability to your website.
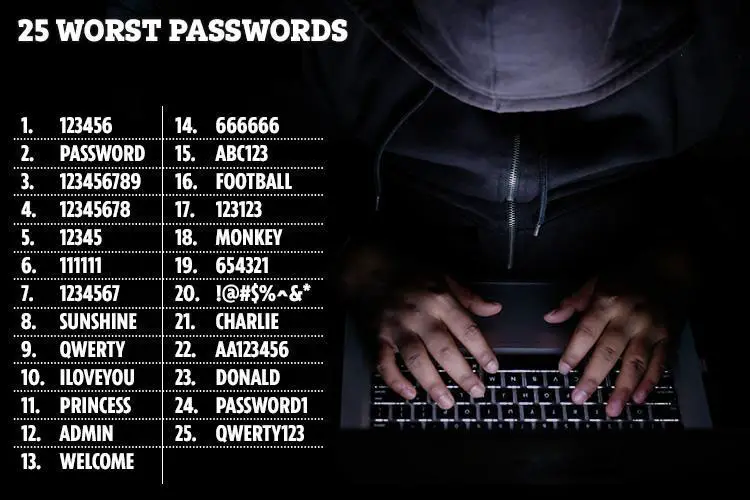
FIX: It is critical that WordPress login passwords use strong passwords, are stored securely and never shared with other installations or platforms. And don't use "admin" as username, choose something that is harder to guess.
Older versions of WordPress used to create a default user with the username ‘admin’, many hackers assume that people are still using the same username.
If you’re still using admin as the username of the administrator account, make a new account on your WordPress site and transfer the ownership of all posts to the new account. Make sure the role of the new user is an administrator.
Once it is done, you can either delete the user account with the username admin or change its role to subscriber.
If your website is a community site with multiple authors, it is better to install https://wordpress.org/plugins/force-strong-passwords/ plugin on your WordPress site. This plugin forces users to use a strong password while creating a new user.
3. Outdated core WordPress, themes or plugins
As with most software, WordPress typically discovers problems that can be used to hack into a website. These issues are typically fixed each time an update is released. But such updates also release the actual WordPress vulnerability to the public.
This means that as soon as an update is released, an exploit will be created to attack websites that have not updated to the latest version.
The same logic applies to WordPress plugins and themes that can exhibit the same problem. This can also happen with PHP software, MySQL software, server software and any other software that has not been updated and exists on your website's server.
Essentially, if any piece of software has not been updated is a sitting duck - a WordPress vulnerability waiting to be exploited.
FIX: Keep all vendor subscriptions active and ensure you keep all components updated to their latest versions.
4. PHP Exploits
Besides exploits that exist in WordPress itself, it is quite possible that a PHP exploit exists in a PHP library that might not have been updated either. The problem with this is that most times, you might not even be aware that such a library is being used on your website.
FIX: For this reason, you should opt for an advanced WordPress hosting such as a VPS or managed WordPress hosting, where you can customize and/or remove PHP libraries on your server that you are not using and do not need.
5. Installing software from dodgy sources
Sometimes, for various shortsighted reasons (possibly monetary), you might consider downloading premium products from "dodgy" sites. In other words, download pirated versions of premium plugins or themes.
This is a sure way to introduce WordPress vulnerabilities to your websites. The reason is that the "price" of using such pirated software is hidden and nefarious. These plugins have usually been tweaked with what is known as a backdoor. Backdoors give users remote control to websites where these plugins have been installed and hackers will have full control of your site and will use it at will for their own practices.

This could include using your website as part of zombie network (network of computers participating in a botnet or DDoS attack), using your website as part of a network of websites used to infect more users with vulnerabilities, to sending SPAM, phishing or other nefarious practices.
FIX: Do avoid such sources and make sure you only download and use software from official trusted sources. Otherwise, you'll surely have hidden WordPress vulnerabilities introduced.
6. Sites not using secure certificates
Sites that do not have an SSL / TLS certificate do not encrypt information being sent between the browser and the server. This means that such information including passwords or other sensitive data such as personal or payment information can be sniffed as it is being transmitted over the internet.
Software exists to read such encrypted data and hoard any potentially valuable information to be used and exploited later.
FIX: By installing and setting up a secure certificate, information is encrypted before being from or to the server
7. File Inclusion Exploits
File Inclusion exploit are some of the most common WordPress vulnerabilities exploited via PHP code. This is when a WordPress vulnerability where a problem in the code allows "elevation of privileges" or "bypassing of security" such that an attacker is able to load files remotely to gain access to a website. Such exploits could completely take over a site or steal private information by accessing information that is not typically available to the public.
FIX: Keep all of your software updated to the latest versions and ensure you have a WordPress security plugin installed
8. SQL Injections
SQL injections are a different form of exploit but this kind of WordPress vulnerability also abuses bugs in code to perform actions that weren't intended. Essentially, an SQL injection occurs when an attacker bypasses normal protections to access the WordPress database and website private data.
By accessing the WordPress database, they can perform abusive changes such as creating administrator-level users that can eventually be used to get full access to the site. Such attacks could also be used to add malicious data to the database such as links to spammy or malicious websites.
SELECT * FROM Users WHERE Name ="" or ""="" AND Pass ="" or ""=""
FIX: Ensure you have the latest versions of software set up on your site and they are kept updated
9. XSS or Cross-site Scripting
This is another very common form of attack. In fact, they are probably the most common exploits.
Cross-site scripting work when an attacker finds ways to trick the victim into loading websites that contain specific Javascript code. These scripts load without the knowledge of the user and are then loaded to be able to read information that they typically would not have access to. For example, such code could be used to sniff data which is entered to a form.
In the rest of this post, we'll take a look at a few strategies to find vulnerabilities in your WordPress website. We’ll also look at various methods to fix WordPress vulnerabilities as well.
Finding WordPress vulnerabilities through scanning
As we said as part of our list above, if you’re looking for free WordPress themes (or any themes or plugins in general) to install on your WordPress website, it is always recommended to pick them from the official WordPress theme directory because the official directory ensures the security of your WordPress themes.
With that said, some legitimate theme developers and agencies prefer not listing their quality free themes in the official directory because the official directory guidelines restrict them to include many functionalities in their theme.
That means, when it comes to choosing a free WordPress theme, the official WordPress themes directory is not the only show in the town. Having said that, when you’re picking a theme outside the official directory, you need to have an extra dose of responsibility in terms of theme assessment.
Below are a few methods to check the authenticity of your WordPress theme and make sure it is secure from potentially malicious codes and WordPress vulnerabilities.
The following services can all be used to check for WordPress vulnerabilities:
- Geekflare
- Sucuri
- Hacker Target
- Detectify
- WPSEC
- Security Ninja
- Pentest-Tools
- WP Neuron
- Quttera
Finding WordPress vulnerabilities after Installation
You might have already installed many themes on your WordPress website. If that’s the case, how would you check the authenticity of the installed themes? A few methods are listed below.
A number of these plugins have not been updated for the last few years and major versions of WordPress. This means that they are probably abandoned and their results are not reliable. Unless you see a recent version, we would suggest that you opt for using Sucuri or another product from our WordPress security plugins list here.
1. Theme Authenticity Checker
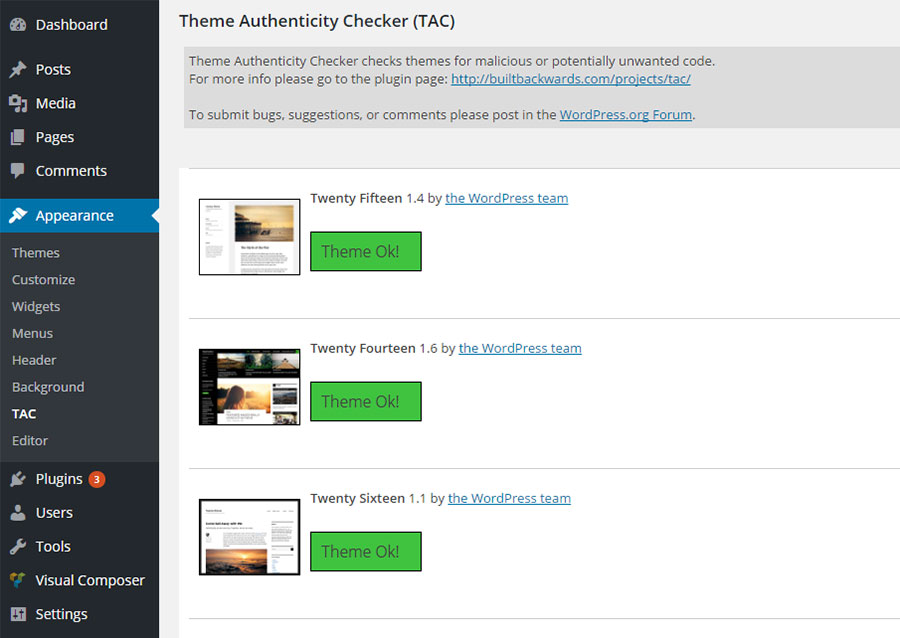
The Theme Authenticity Checker is a free plugin that allows you to scan the theme files to find if there are any WordPress vulnerability issues that you need to be aware of. If potentially malicious code is found in an installed theme, the plugin will tell you the patch, the line number and displays the suspect code. This will help you take preventive action - or get rid of the theme.
This plugin is great to check whether the installed theme has had any encoded malicious script inserted into it without your knowledge.
Unfortunately, this plugin hasn't been updated for the last 3 years now, so until you see a more recent update, you might want to skip this.
2. WP Authenticity Checker
On a similar vein is the WP Authenticity Checker. Besides checking for problems with themes, this plugin also looks at problems with the WordPress core or 3rd part plugins to identify any WordPress vulnerability.
Unfortunately, this plugin has not been updated for the last 2 years as well, so you might not want to fully trust the results of this plugin.

Simple download it, install it and run to discover any problems with any themes or plugins.
3. Exploit Scanner
The Exploit scanner also was a product which operated in a similar way, but unfortunately, this plugin has also fallen into abandonment. For this reason, it is not recommended that you use it unless you see a fairly recent update.
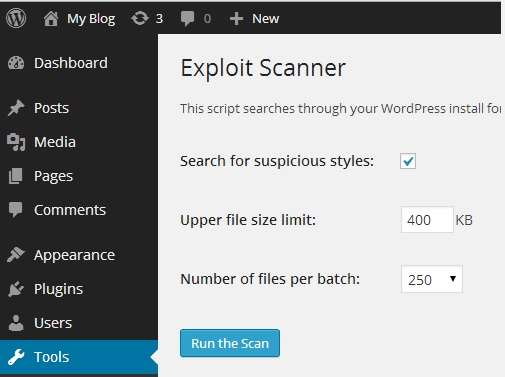
Exploit Scanner is another free plugin, which offers more robust features than TAC. The best thing is that the exploit scanner plugin helps you check the database of your WordPress installation besides the theme files.
Please note that these plugins will only show you the vulnerability and it is up to you to decide what preventive measures you should take to eradicate the WordPress vulnerability.
Additional Fixes to Protect from WordPress Vulnerabilities
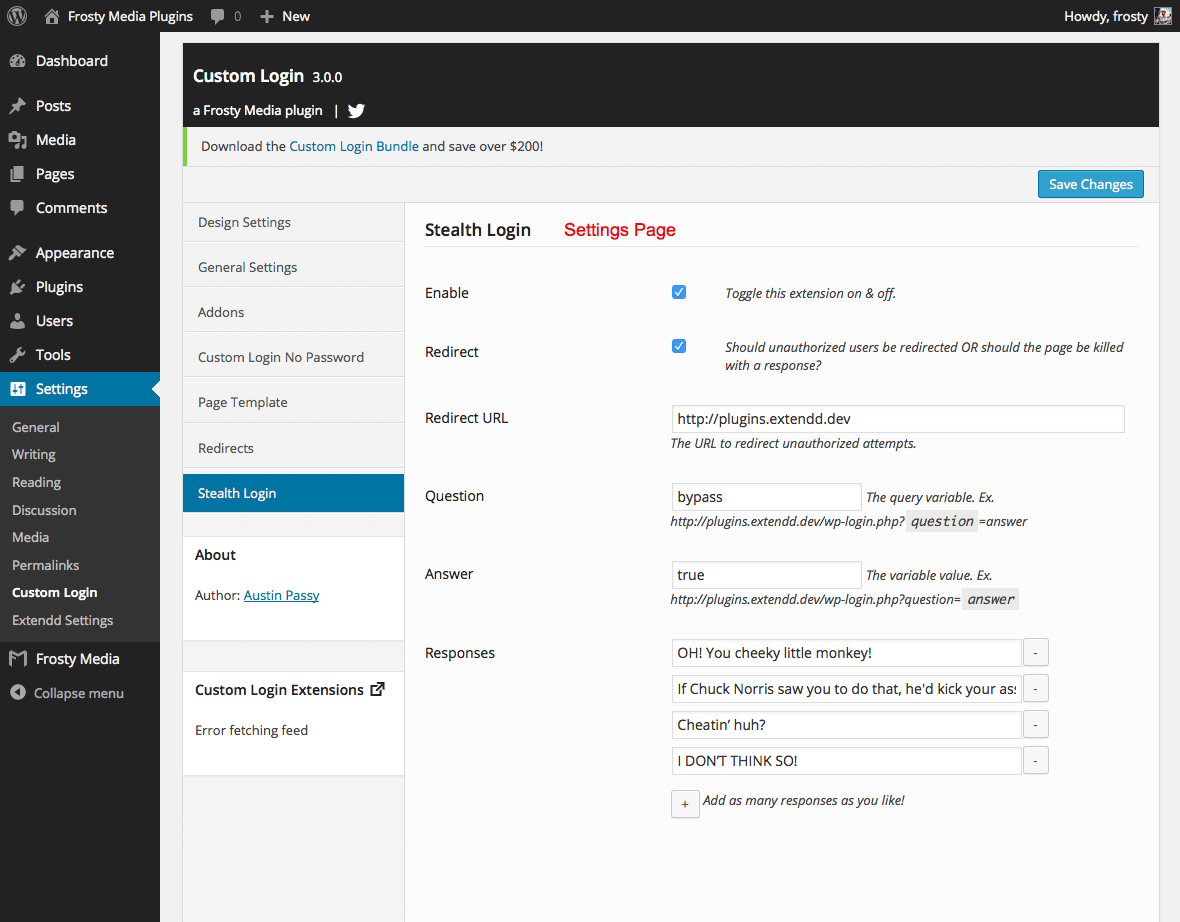
1. Set a custom login URL for WordPress
During WordPress installation, WordPress creates two login URLs by default. They are
- wp-login.php
- wp-admin.php
The problem with using the default login URL is that anyone can log in to your WordPress dashboard once they find (or makes the right guess) the username and password. By customizing the URL of your login page, you’re stepping towards better security for your WordPress website and making it harder for bad guys to break it.
How would you change the login URL of your WordPress website?
Simply install the Stealth Login plugin and customize the Stealth part of the Custom Login plugin to hide the login.
2. Limit the number of login attempts
So you’ve customized the login URL of your WordPress website for better security. But what if the bad guys discovered the actual login URL? Then, how can you prevent attempted entries to your website?
In such a case, one of the best methods is to limit the number of login attempts. By default, hackers can try as many as passwords to enter into your website as they want; by limiting the login attempts, you’re blocking this possibility of brute force attacks to your website.
Install iThemes Security (a full-blown security plugin) or Login LockDown plugin. Both these plugins allow you to restrict the attempts a user can make to enter into the dashboard.
3. Disable directory browsing
By default when your visitor navigates to a page and the webserver can’t find an index file for it, automatically it displays a page and shows the contents of the directory. The problem with this is that anyone can navigate into those directories, which can be vulnerable for your site and a hacker could exploit it easily to take your site down.
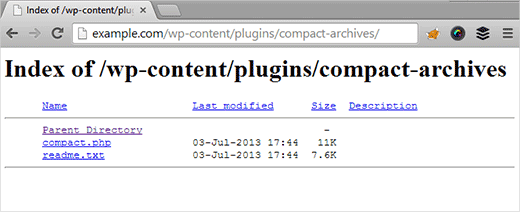
For instance, some WordPress directories contain sensitive data such as wp-content or wp-includes. By allowing hackers to navigate through these folders, hackers could find potential exploits in it.
So it is important for your website’s security to disable directory browsing.
How would you disable directory browsing on your WordPress website?
The only thing you need to do is to add the code below at the bottom of the .htaccess file of your WordPress website.
Options -Indexes
Note: Make sure you take a backup of your website before making any changes to it. .htaccess is a hidden file, and if you cannot find it on your server, you need to make sure that you have enabled your FTP client to show hidden files.
Recommended reading: Native vs. Plugin- Taking WordPress backups with different methods
Once you disable directory browsing, all those directories that were previously visible will start showing a ‘404 Not Found’ page or ‘403 Access Forbidden’ message.
Conclusion
No software is perfect when it comes to security. That’s true even for WordPress, so make sure you update the WordPress core software or any themes and plugins whenever there are releases of new versions to stop any fixed WordPress vulnerability. Make sure you enable automatic updating of WordPress or have a process in place to keep it updated.
Need help getting your WordPress fixed and cleaned? Try these top-rated affordable gigs on Fiverr!
Click here to find experts on WordPress speed optimization.
Click here to create a full WordPress website.
If you have any questions, ask below in the comments section, and we’ll do our level best to help you out.



